Active Directory (AD) vs Azure Active Directory (AAD)
This article describes the main difference between Active Directory and Azure Active Directory
Information in this article applies to Safetica ONE 10 or older.
It is one of the very common questions is: Is Azure AD the same as AD? Can I replace it? The short and simple answer is no. However, it is more complicated. That's why this article is formed. Let's have a look at similarities, differences, and combinations.
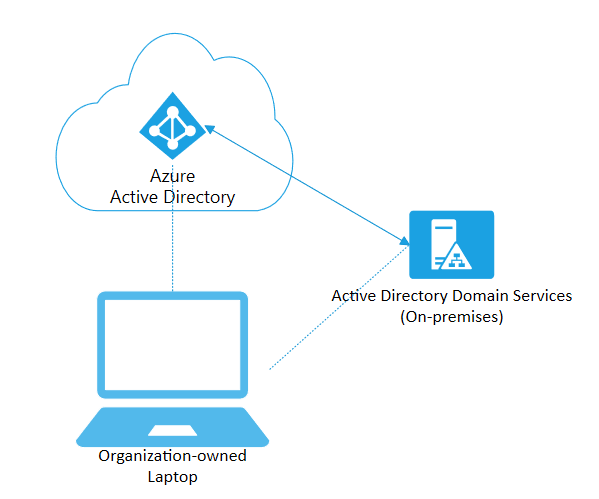
Active Directory Domain service
Active Directory Domain service is basically a database, where you can have all your computers, users and others organized. It provides authentication and authorization to applications, file services, printers, and more on-premises resources. AD uses protocols such as NTLM and Kerberos for authentification and LDAP for resource discovery. With a great feature Group policy, you can distribute settings throughout a whole network. There are many security groups, user and admin accounts, passwords, identity and access rights, and that's why securing AD is the key. Nevertheless, the important point of view is that AD was not designed to cope with the world of web-based Internet services.
Azure Active Directory
First, Azure Active Directory is not Active Directory, unfortunately, its name leads to much confusion. However, AAD has a similar function with the authentification and authorization of applications. Compared with AD, Azure Active Directory was designed to support web-based services that use RESTful interfaces for Office 365, Google Apps, etc. It also uses different protocols for working with these services (SAML, OAuth 2.0.). You could say that AAD is an "AD service in the cloud". Another difference is that there is no such thing in AAD as forests and domains. Instead, you are a tenant representing your whole organization and you can manage all users with their passwords, permissions, etc. A user with one identity can sign on to thousands of SaaS applications and not just into Microsoft's Office 365, Sharepoint or Exchange online. And he can do it without a repeated requirement to log in.
Conclusion
Hopefully, it is more clear now that AAD is different from AD. For example, in AAD there is no such thing as Group Policy or support of LDAP, but you can find many other brand-new features. Nowadays, there are various models of using Active Directory services and every company has different needs and possibilities. In case your organization doesn't need the missing features of AD, you can move to Azure Active Directory and decommission the classic Active Directory. There are various scenarios containing Hybrid Azure AD, which means combinations of AD and AAD. This type of architecture offers a combination of both and thanks to Azure AD Connect your user/password data are synchronized. In the end, you can use just classic AD, however, you can hear every day more and more about the advantages of moving to the cloud. For more verbose information, you can visit the official websites of Microsoft.
AD vs AAD vs Safetica
In case your environment is using both AD and AAD, Safetica is able to collect data from both tools. This is possible via connection to Active Directory, which provides data from AAD. Active directory is serving as a connector between Safetica and Azure Active Directory. However, if you are using AAD only, Safetica is unable to collect data.
