Detection of risky operations in Safetica 10
Identify potentially dangerous operations with just one glance.
Information in this article applies to Safetica 10 or older.
To support our Insider Threat Protection shift, Safetica 10 now allows you to detect risky events based on a set of pre-configured detection rules. These rules are the same as in our SaaS product Safetica NXT, so that all our customers may enjoy this new feature.
Our detection rules are based on combinations of various attributes of outgoing operations (e.g. destination type) and they evaluate as risky all the usual suspects, such as text files uploaded from a local drive to a website outside the secure company perimeter.
Safetica Discovery allows you to detect threats, but only by upgrading to Safetica Protection or Safetica Enterprise will you be able to block them.
In this article, you will learn about:
- The relationship between risk detection rules, DLP policies. and safe zones
- What does the admin see in logs
- Where to visualize risky operations
Can detection rules be modified and how do they relate to DLP policies?
DLP policies and safe zones have priority over our pre-configured detection rules.
The pre-configured detection rules themselves cannot be modified, but you can customize risk detection by modifying your safe zones or creating Allow DLP policies.
Files with destinations within a safe zone and files evaluated by DLP policies as Allow are considered “not risky”, even when they hit a pre-configured detection rule.
What does the admin see in logs?
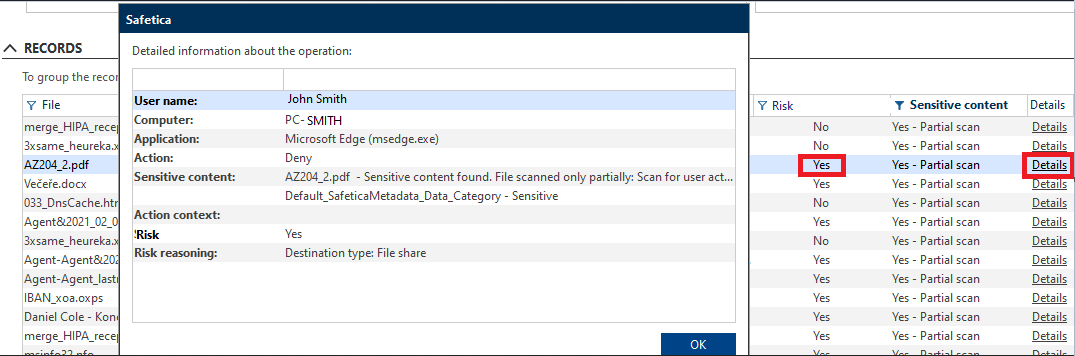
To see what events are considered risky, you can check the Risk column in:
WebSafetica > Dataflow > Outgoing data
WebSafetica > Dataflow > All dataflow
Safetica Management Console > Discovery > Files
Safetica Management Console > Protection > DLP logs
By filtering only risky events (the Yes option in the Risk column), you will find all your “usual suspects”.
Click the Details link in the Details column to see the reasons, why an event was identified as risky.
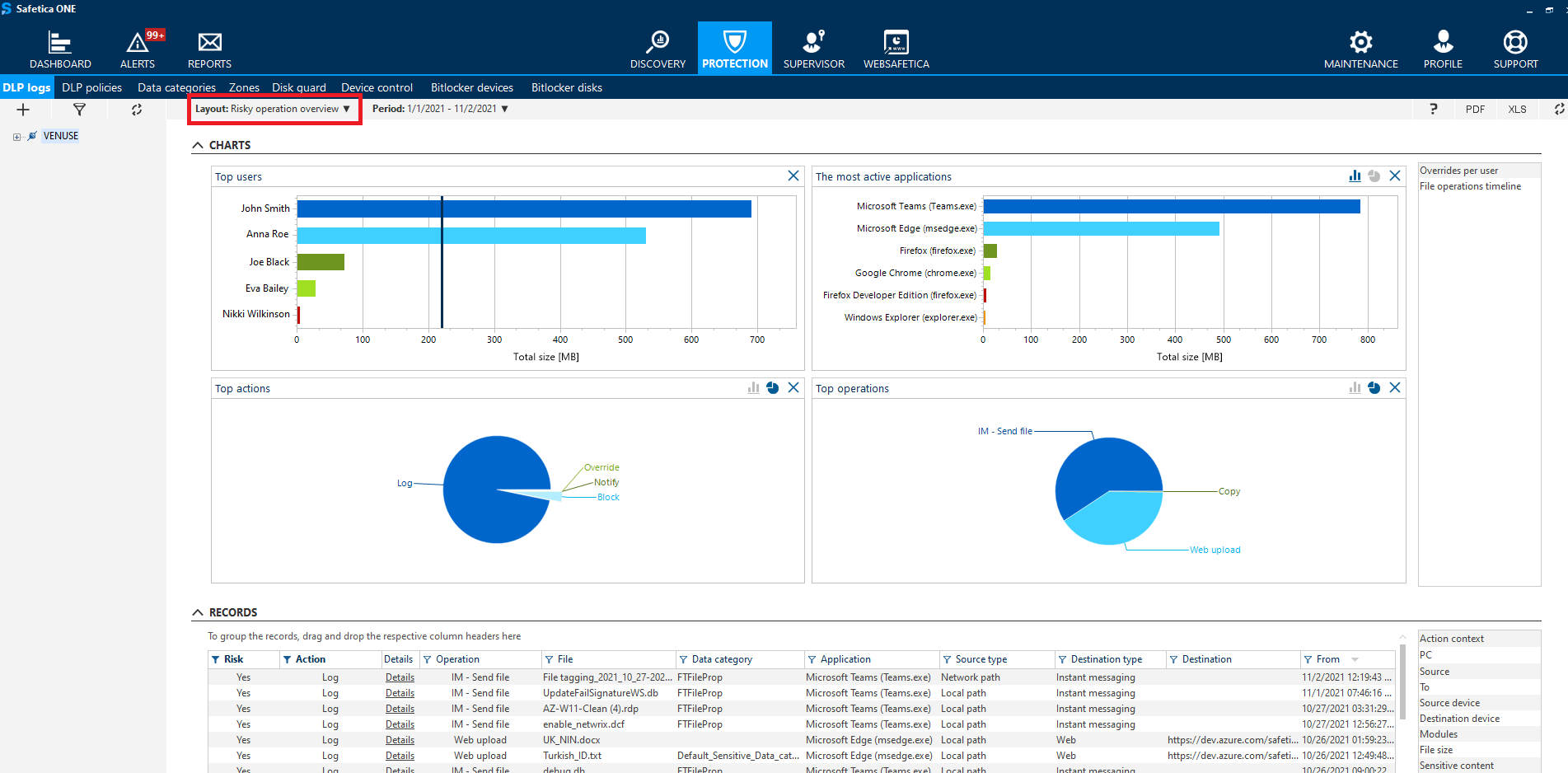
Where to visualize risky operations
To see information about risky operations in the form of charts, go to Protection > DLP logs and in the upper left part of the screen select Risky operation overview from the Layout drop-down. You will see who performed risky operations, via which applications, what operations were risky and whether they were logged, blocked, or overridden.