How to work with the DLP policy rule for Local paths
Information in this article applies to Safetica ONE 10 or older.
The Local path policy rule is available in Safetica Enterprise only.
In this article, you will learn:
- What is the Local paths policy rule
- Limitations
- How to add the Local path rule into a policy
- How not to use the rule
What is the Local paths policy rule
Safetica ONE offers a wide range of DLP policy rules that cover the most common channels through which sensitive data might leak. Most of these rules focus on protecting data from leaving the secure company environment. One exception is the Local paths rule which restricts the movement of sensitive data within the company. You can use it for example to restrict file transfers into folders shared between multiple users.
Local paths is an expert DLP policy rule with specific behavior. If set incorrectly, it can negatively affect user workflow. Before using it, please consult your scenario with Safetica Support.
Limitations
When creating a DLP policy with the Local paths rule, there are limitations to consider:
- The rule is only available for data categories of the context type.
- When using the rule, you cannot set up Override or the Shadow Copy feature.
How to add the Local path rule into a policy
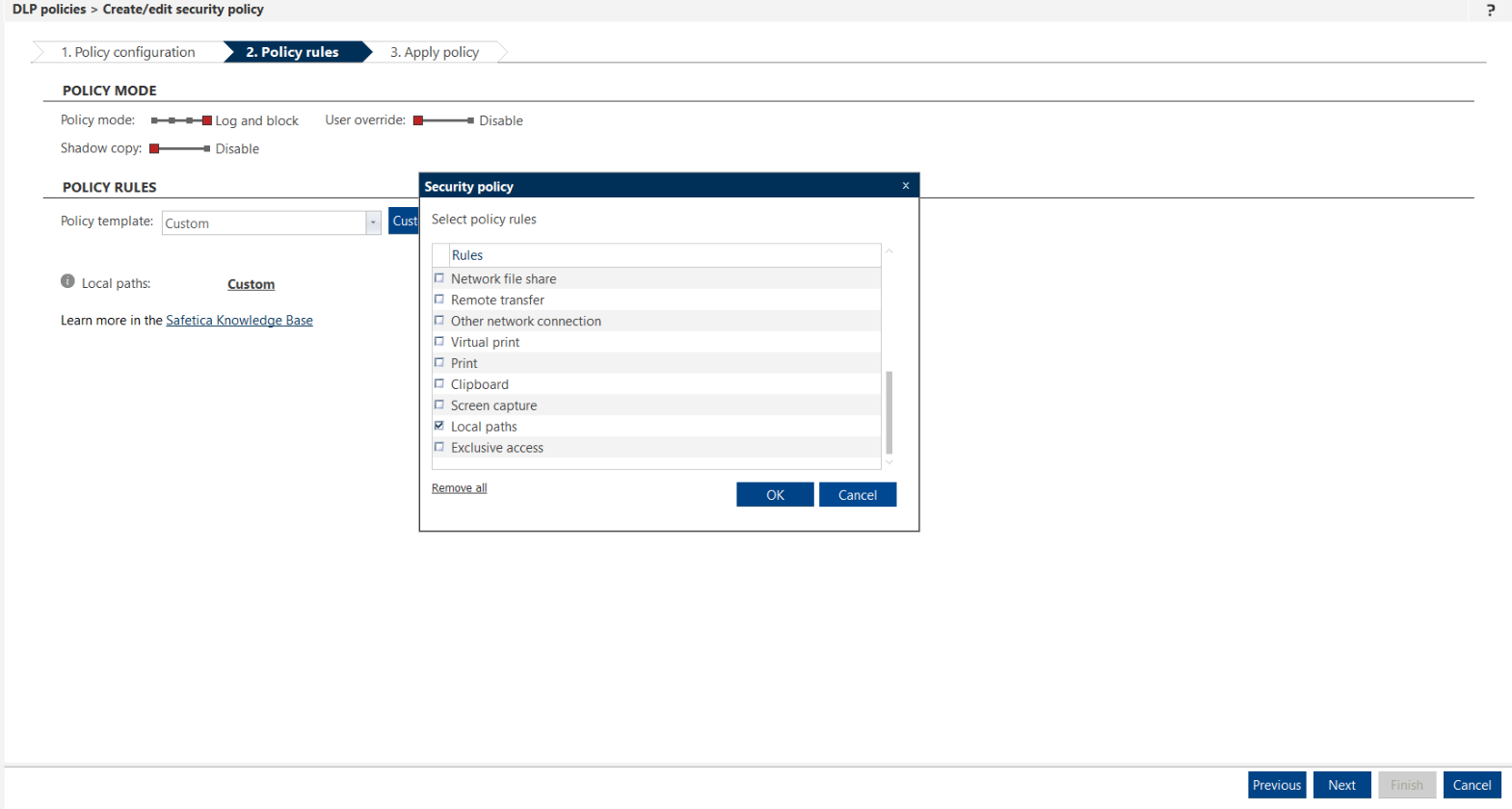
You can add the Local paths rule to your policy via the Customize button, where you can select it from the list of available rules.
1. In Safetica Management Console, go to Protection > DLP policies.
2. Click New policy.
3. With the Policy type slider, select Data.
4. Click Add category and select a context data category. Click Next.
5. Click Customize and select the Local paths rule.
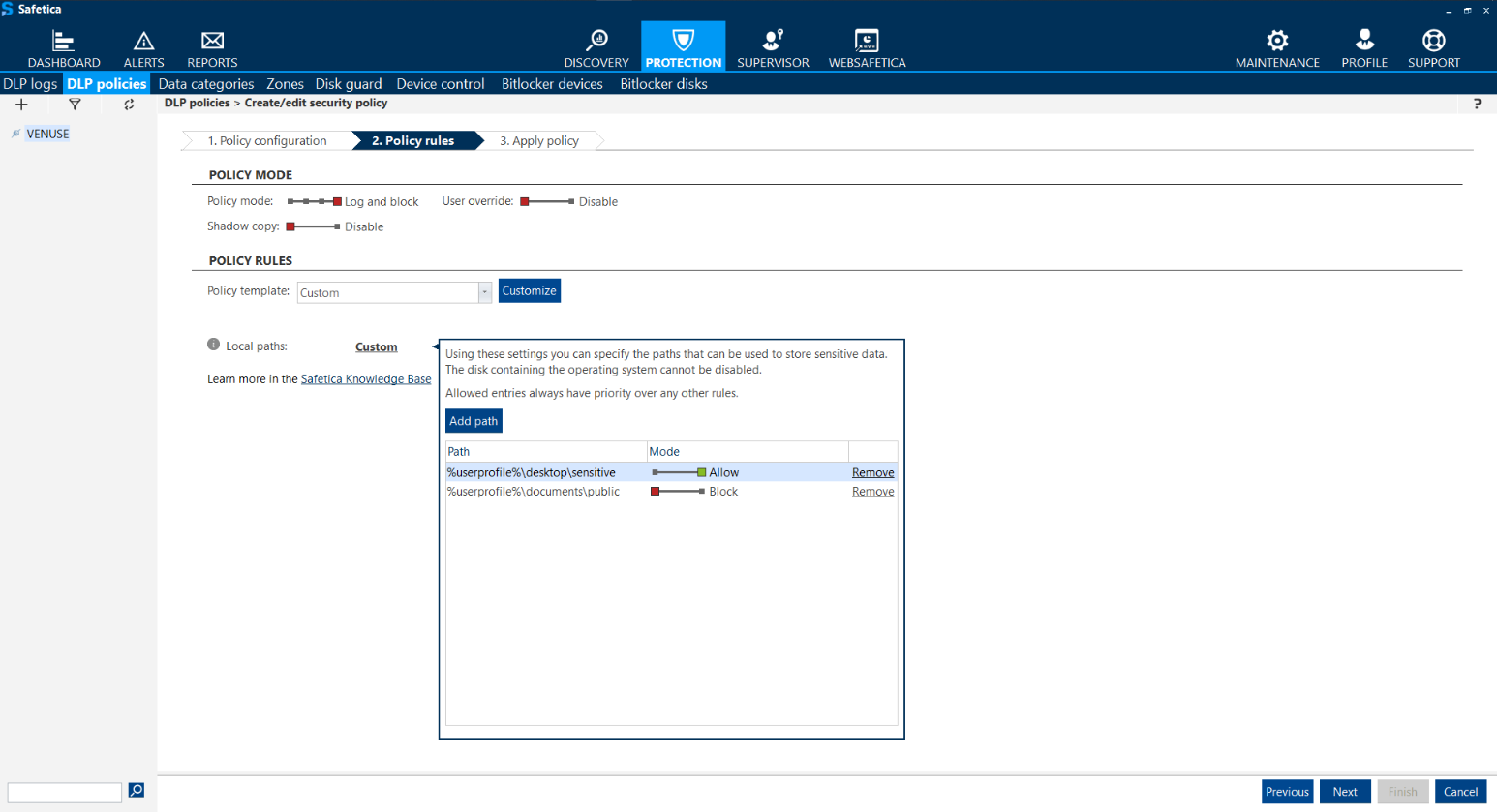
After you include the rule in your DLP policy, you have to specify restrictions for local directories, where the data can or cannot be stored.
6. Click Custom and add the desired local paths.
When entering a path, you can insert it with a %variable%, in order to apply it to individual users.
How not to use the rule
- This rule was not designed and should not be used for restricting file transfer from network shares to local drives (which are considered to be internal safe storages). Safetica policies are designed with potential data leaks in mind. Therefore, the file transfer within internal environment is not considered a data leak.
- Blocking the whole internal drive (such as as C:/ ) may lead to unexpected behavior and crashes of applications, since many use local drive to store temporary files necessary for their correct functioning. For this reason, we do not recommend using this rule in such manner. Before using this rule, we recommend getting in touch with Safetica Support to discuss the configuration.