Git control in Safetica
The Git policy rule enables companies to protect another channel – the Git versioning system.
Information in this article applies to Safetica ONE 10 or older.
The admin can now easily determine whether to allow the use of git push and also select into which Git repositories can data be pushed from local directories. The feature logs and controls only data upload into remote Git repositories (git push). Data download (git pull or git fetch) is ignored. This way, data leaving the endpoint is protected while user workflow is not impaired.
The Git policy rule is only available for General DLP policies, which now include a new Git rule. For now, the Shadow Copy and User override features are not available for this data channel.
In this article you will learn:
Controlling git push in general
If you want to control git push (data upload to Git) in general for a specific user, a group of users, or the whole company, create a general policy with rules for Git in Safetica Management Console:
- Go to Protection > DLP policies and click New policy.
- Name the policy and for Policy type select General. Click
- Choose the Policy mode. You can select whether to log the action, notify the user that the action might be dangerous, or completely block the action.
- In Policy rules, find the Git slider and select the desired option. Click Next.
- Add users to whom the policy will be applied and click Finish.
- Confirm by clicking
 in the upper right corner.
in the upper right corner.
Controlling git push for specific repositories
To create policies for individual Git repositories, use Safetica Zones in Safetica Management Console. Go to Protection > Zones and add the desired repositories into them. Each zone is a list that you can later use to create DLP policies.
How to add a repository into a zone?
- Go to Protection > Zones and click Add zone.
- Name the zone and decide whether you consider the repositories added to it to be safe. Repositories added into a Safe zone will not be restricted at all.
- Click OK.
- In the list on the left, select the newly created zone and click Add item.
- To add a repository, click Web address.
- Enter the repository address into the Web address line and click Add.
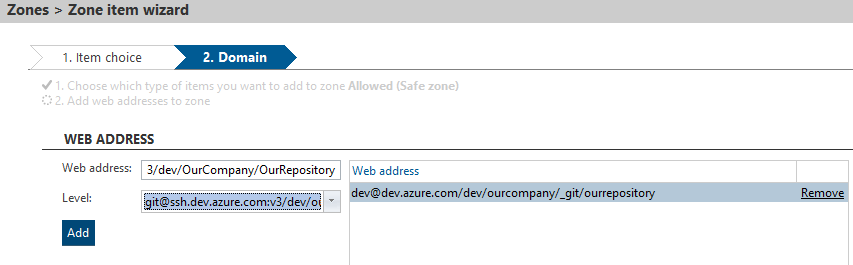
You can use either the https or the ssh protocols. Each of them, however, uses their own address format. To allow/block the connection to a repository both via https and via ssh, you must insert each address separately.
Example of https format: https://dev@dev.azure.com/dev/OurCompany/_git/OurRepository/
Example of ssh format: git@ssh.dev.azure.com:v3/dev/OurCompany/OurRepository
For Safetica ONE 10.1 and newer:
- All repositories added into zones are automatically converted to lowercase
- Format for allowing/blocking access to a whole repository: *.bitbucket.org/user_name/repostiory.git/*
- Format for allowing/blocking access for a specific user: *.username@bitbucket.org/ user_name/repostiory.git/*
- To add the wildcard characters, use the Level dropdown menu
7. Confirm with Finish.
8. Confirm by clicking  in the upper right corner.
in the upper right corner.
How to use zones to control git push for specific repositories?
The created zone can be used when setting up DLP policies to control data pushed into Git repositories:
- Go to Protection > DLP policies and click New policy.
- Name the policy and for Policy type select General. Click
- Choose the Policy mode.
- In Policy rules, find the Git slider and choose Safe zones allowed.
- On the next page, add users to whom the policy will be applied and click Finish.
- Confirm by clicking
 in the upper right corner.
in the upper right corner.
What does the user see?
When a user tries to push data into a blocked Git repository, they will be shown a notification that the action is forbidden and was blocked.
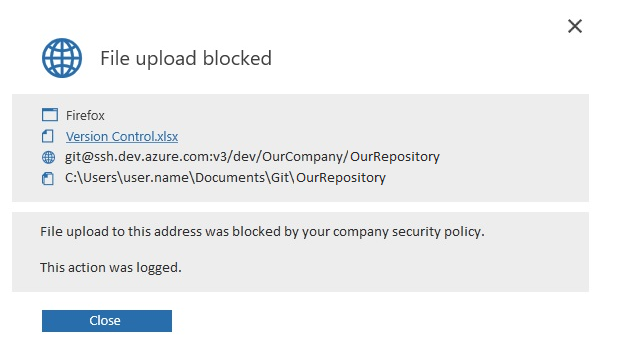
Which repositories were blocked by Safetica?
To find out for which repositories git push was allowed or blocked, go to Protection > DLP logs. In the Records table, filter out Git push in the Operation column. You will see the address of the Git repository, the path to the local synced directory, who initiated the git push, whether the git push was allowed, blocked, or logged, and many other details.
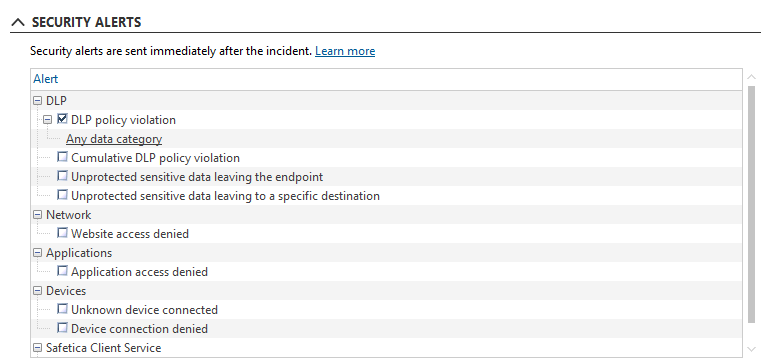
Alerts
Admins can also set real-time alerts which notify them about potentially dangerous or undesirable user activities as they arise. Notifications about git push are sent as part of the DLP policy violation alert. The admin can set it up in Safetica Management Console > Alerts after clicking the New rule button.