Overview of digital certificate use in Safetica
Information in this article applies to Safetica ONE 10 or older.
Safetica integrates into network communication in order to ensure detection or restrictions of user actions occurring on the network. By default, Safetica uses its own self-signed digital certificates. These provide a basic level of security by using 256-bit AES encryption, however, companies can increase this security level by replacing the self-signed certificates with their own, digitally trusted ones.
The company’s root certificate is only used to create and sign an intermediate certificate which is then imported into Safetica’s Management Service. Each Safetica-protected endpoint then receives a subordinate certificate which is signed by the parent one imported into the SMS. Only these certificates are used on the endpoints, the root certificate does not enter Safetica’s communication directly. You can check the following diagram to understand the hierarchy better.
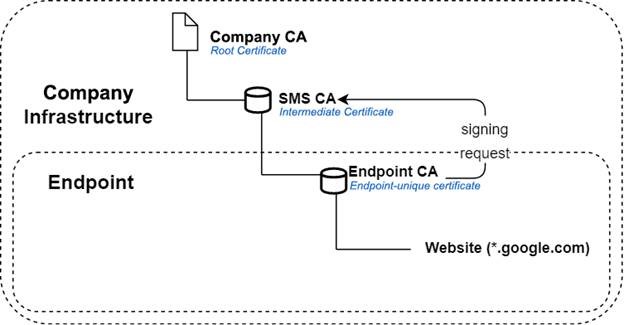
In case the root certificate is revoked, the entire subordinate chain of certificates becomes untrusted. In case the generated certificates expire, Safetica reverts to its default setting of using self-signed certificates but the endpoints remain functional, only the network communication is no longer part of the trusted certificate chain. You can set up an alert to be notified about such expiration or other certificate-related issues.
To learn more about properly configuring Safetica for use with a company’s root certificates, refer to article Configuring Safetica to sign its network communication by a company’s root digital certificate.
