Find out more about protected users
In the User behavior section, you can see all your users listed from the most risky to the least. If you wonder why a user was assigned a certain risk, you can look into their detail ![]() .
.
The detection of user risk is automatic in Safetica NXT. To fine-tune it, you can:
- adjust protection policies and data classifications, which allows you to specify and protect sensitive data in your company
- visit the Destination section and adjust Safe and Untrusted destinations
- visit the Shadow IT section and decide which app and website activities are considered risky or safe in your company
In User behavior, you can:
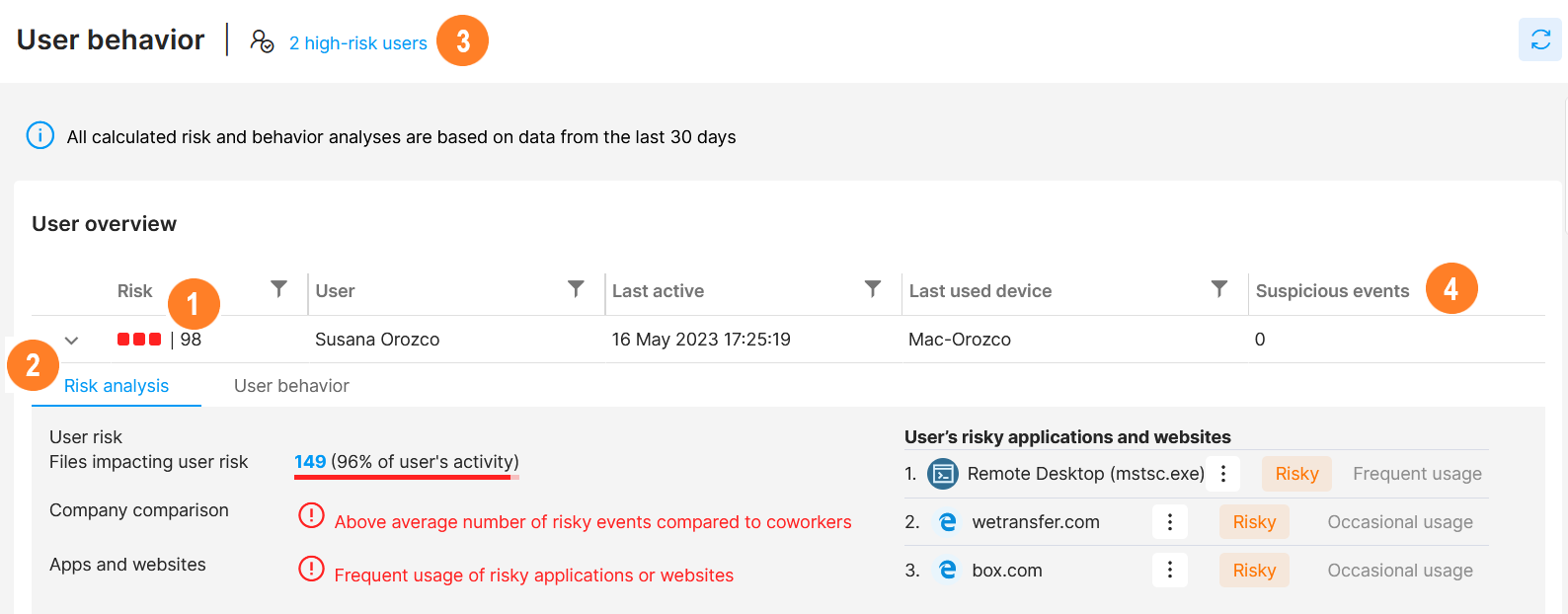
![]() see the risk of individual users
see the risk of individual users
A user's risk is a numerical evaluation assigned to each user based on their activity. The higher the number, the more suspicious is the user's activity. It may serve as a signal that a deeper analysis of the user's behavior might be needed.
![]() see each user's detail:
see each user's detail:
-
- Risk analysis tab - more detailed reasoning for the user's risk and a list of their top risky app and website activities.
Click the Files impacting user risk number to see all the files that influenced that particular user's risk.
-
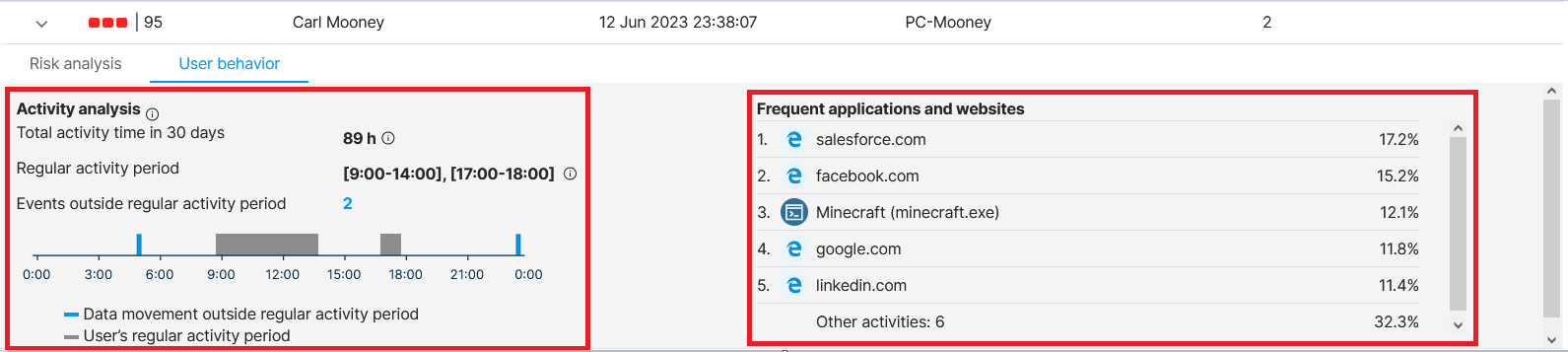
- User behavior tab - on the left, there is Activity analysis - analysis of the general period in which the user works + events that happened outside their regular working hours. On the right, there is a list of the most frequently visited apps and websites of that user.
![]() click the link to filter out high-risk users
click the link to filter out high-risk users
![]() see when and on which device the user was last active and what data-related suspicious events they performed
see when and on which device the user was last active and what data-related suspicious events they performed
Want to learn more? Read next:
Data security: What is risk level in Safetica NXT