See at first sight the harmful activities happening in our company.
In this article, you will learn about:
- What will you see in Shadow IT
- How to mark activities as risky or safe
- How to see events tied to a specific activity
- How to see on which devices a specific activity was performed
- The Personal usage tab
What will you see in Shadow IT
Shadow IT highlights risky company activities related to application and website use. New or risky activities are highlighted by default. The admin can fine-tune what is considered a company activity and whether risk is assigned properly.
Company activities can be backtracked to specific devices and users.
If there are any activities that do not show up in the Company activities tab, try looking into the Personal usage tab.
How to mark activities as risky or safe
Safetica NXT smart analysis adds info about apps and websites being:
- New - never used in the company before. Status New disappears after 7 days or after the admin manually marks the activity either Safe or Risky.
- Safe - apps and websites that are common in your environment (e.g. the Teams app can be marked as Safe).
- Risky - to see why an activity was assessed as Risky, hover your cursor over the Risky label.
To use Shadow IT to its full potential and see at first sight the harmful activities in your company, you should also leverage your own knowledge and add or remove risk manually - just click in the Activity column and choose the appropriate option.
Activities marked both New and Risky are especially important for admins to check.
To easily filter risky, safe, neutral, known, and new activities, you can click the widgets at the top of the page.
Changing the risk of an app or website also affects the user risk of those who participate in the given activity.
To see the risky apps and websites a specific user used, open their detail in User behavior.
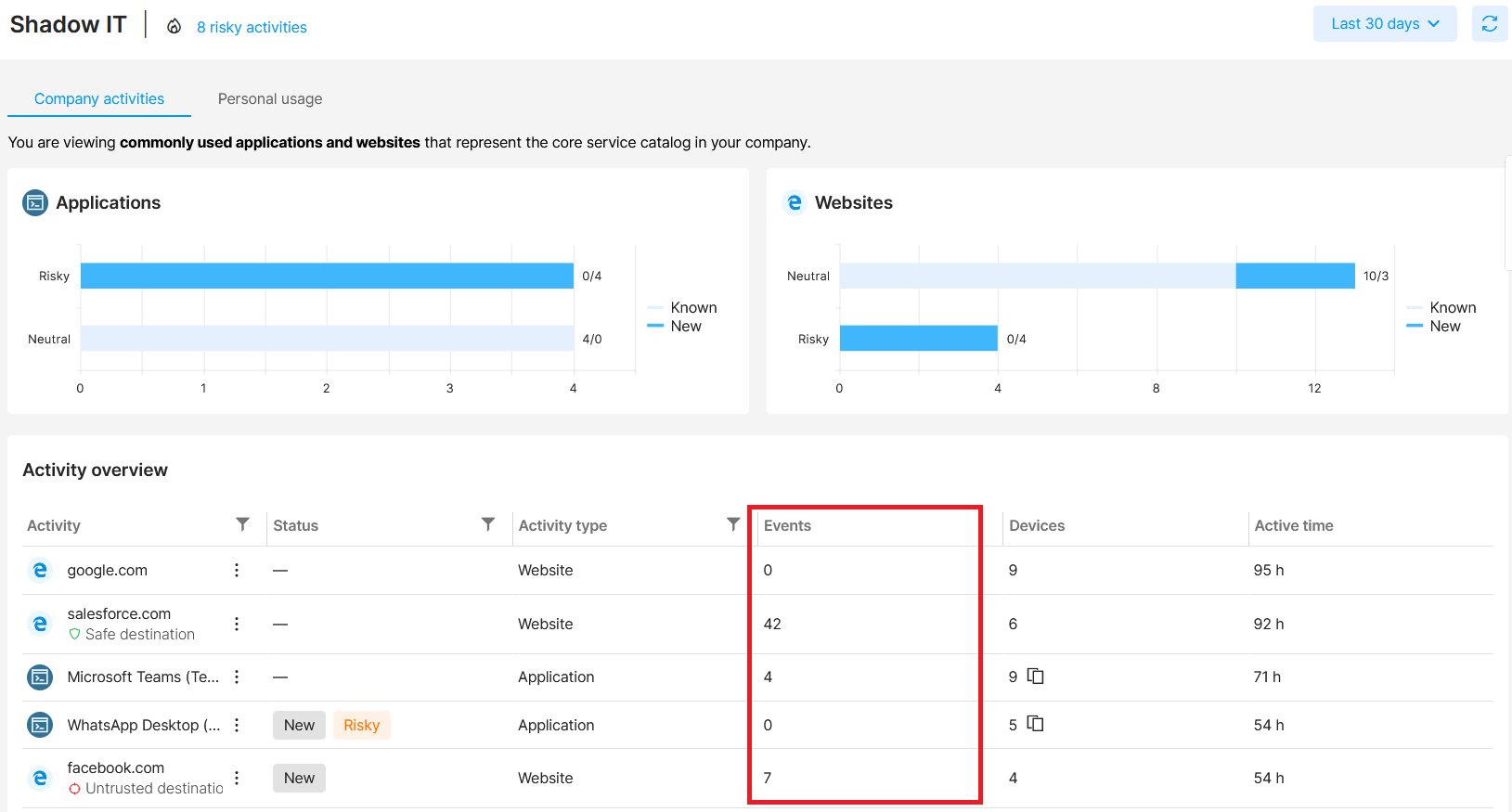
How to see events tied to a specific activity
Info from Shadow IT is tied to Data security.
In the Events column, you can see the number of data security events tied to that specific activity. Click the number to list all the events and see their details in the Data security section.
Example: You see a suspicious app (e.g. Facebook) is used by employees. It is not marked as Risky, but there are several security events tied to it. To see what they were, click the number in the Events column. You will be taken to the Data security section with filtered uploads to Facebook. This way, you can easily see if someone is uploading company info (e.g. screenshots) to Facebook.
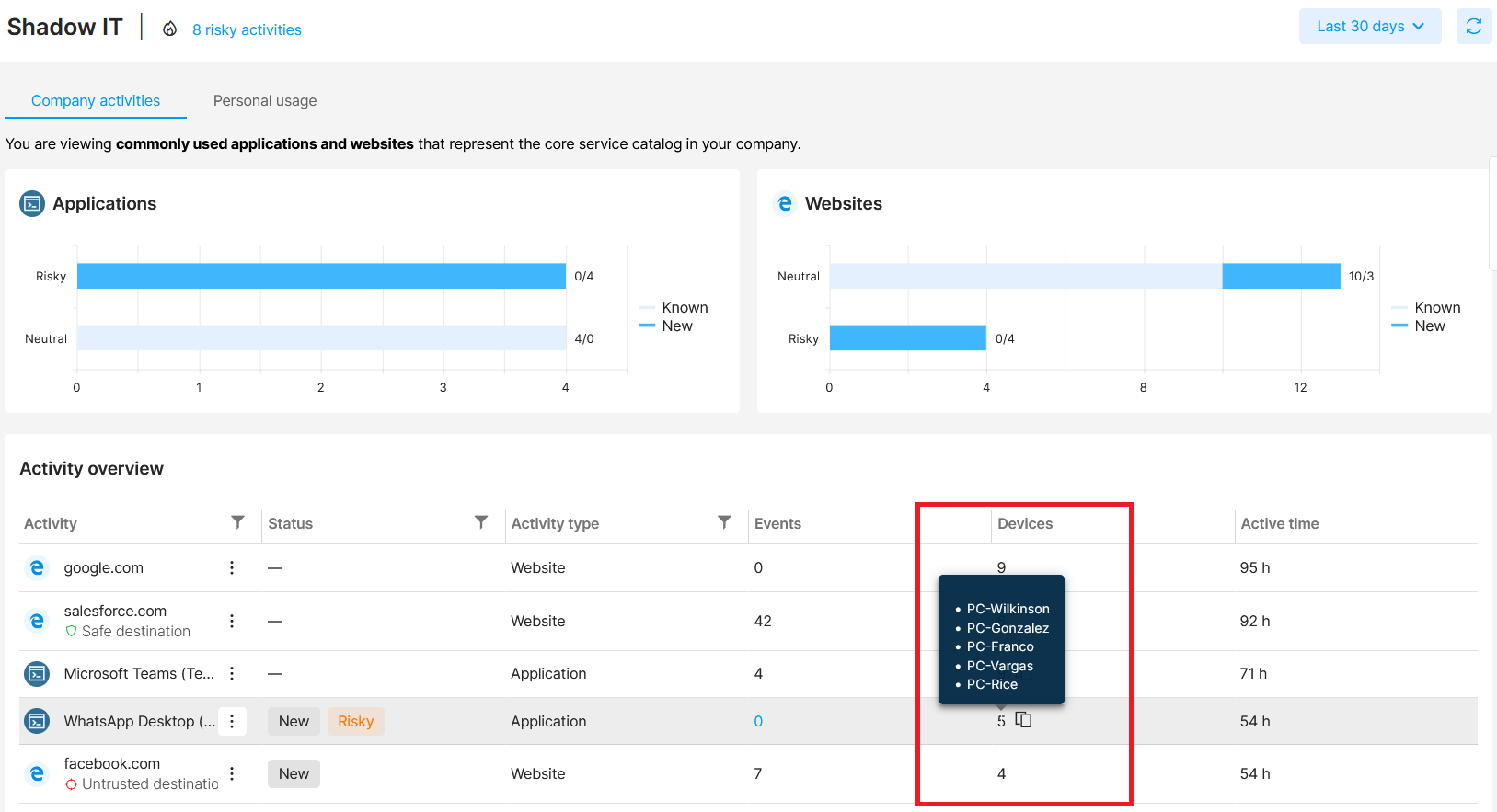
How to see on which devices a specific activity was performed
In the Devices column, you can see the number of devices where the activity occurred. To see the specific device names, hover over the number with your cursor. You can copy the list of devices by clicking the  icon. Please note that the list of devices is only shown for application-related activities.
icon. Please note that the list of devices is only shown for application-related activities.
Example: Twitter was visited on 7 different devices, but only 2 data security events were detected. It might be a good idea to set this activity as Risky since there could be even more events in the future.
The Personal usage tab
Activities that do not show up in the Company activities tab, can be found in the Personal usage tab. In general, these activities are not related to data security and are only used by a few users in short time periods (e.g. short web browsing).
Information in Personal usage tab may be personal (e.g. personal web browsing, leisure activities), and you might breach users’ privacy by viewing it.
If you mark an activity as Risky, it will be moved to company activities, and you will start seeing more details.
Please keep in mind that such a change will affect user risk.