✨Cloud-hosted Safetica: Risk assessment
❗For now, risk assessment is only available in cloud-hosted Safetica. It is not yet available in Safetica hosted on-premises.
In this article, you will learn:
- What is risk assessment in Safetica
- Which factors influence risk assessment
- Where can I find info about risk assessment
- How to set up alerts for risky operations
Introduction: What is risk assessment in Safetica
In cloud-hosted Safetica, each file operation is assigned risk based on how likely it is to cause a data leak. Safetica uses four risk levels when assessing each file operation: high, medium, low, or none. For example, sending data via email might be a low-risk operation, while uploading data from a network drive to webmail should be considered a high-risk operation.
Benefits of risk assessment
- Highlights file operations that are important to investigate.
- Solves problems with too many records. With highlighted risk assessment, admins can be sure they focus on real incidents and be less worried about overlooking something.
- Helps with Safetica configuration (for example, what to add to safe or untrusted destinations).
Which factors influence risk assessment
Risk assessment is determined by Safetica smart analysis, and it is the combination of the following factors:
- The operation occurred at an unusual time, outside the user’s regular activity period (risk increase). The user’s regular activity period is not fixed. Safetica considers every individual's personal activity period and factors in things like time zones or different work styles.
- File contains sensitive data (risk increase).
- File is considered “valuable” based on its extension (risk increase).
- File is transferred using a risky application or website (risk increase). Apps and websites that are risky by default (the list is predefined and cannot be changed): remote access apps, alternative web browsers, data encryption apps, file hosting websites, illegal websites, proxy websites, FTP clients, screen capture apps, P2P file sharing apps, encrypted messaging apps, SSH clients, etc.
- File is transferred to an untrusted destination (risk increase). Untrusted destinations can be set up by the admin in Data destinations. Destinations that are untrusted by default: facebook.com, tiktok.com, whatsapp.com, wetransfer.com, simplyhired.com, youtube.com, etc.
- File is transferred to an uncommon destination that has otherwise been rarely used by the user or in the company in the last 30 days (risk increase). For example, if the company rarely uses USBs and suddenly a user copies a lot of data to a USB, it will be considered risky.
- File is transferred to a destination that is considered safe (risk decrease). Safe destinations can be set up by the admin in Data destinations.
Where can I find info about risk assessment
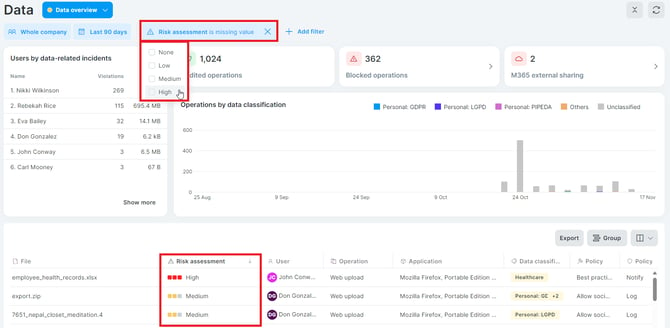
To see how risky individual file operations were, go to the Data section and look at the Risk assessment column. Risk assessment is indicated by colors:
![]() High
High
![]() Medium
Medium
![]() Low
Low
![]() None
None
You can also filter out file operations based on risk assessment - click the Add filter button, select Risk assessment, and then select High, Medium, Low, or None.
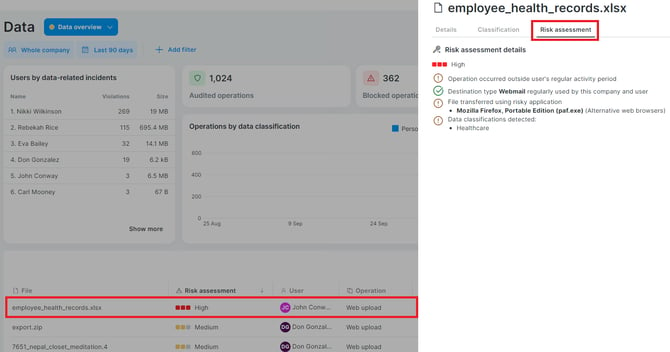
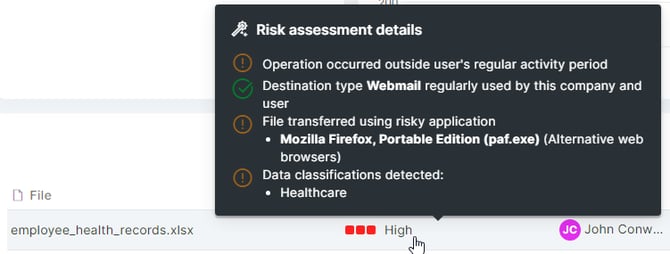
To see the detailed reasons why a file operation was considered high, medium, or low-risk, you can:
- Hover the mouse over the risk assessment of that file operation:
- Click the file to open its detail and go to the Risk assessment tab:
How to set up email alerts for risky operations
If you want to be informed about every operation that is considered risky in real-time, follow the steps mentioned here.