External device policies: How to block the use of selected external devices
Safetica can prevent users from using certain external devices. Discover how to effectively utilize this feature to prevent data leaks and bolster your company's security
In this article, you will learn about:
- What are external device policies
- How to create a policy that controls selected external devices
- How to find records of blocked or connected devices
- Example: Blocking file transfers to USB and Bluetooth devices that are not considered safe by the company
- FAQ
Introduction: What are external device policies
External device policies help you very granularly control the connection and use of external devices (such as USB devices, Windows Portable Devices, or Bluetooth devices).
🍏macOS devices: For now, Safetica only audits and protects USB storage devices.
Learn more about the differences in features between Windows and macOS here.
External device policies in action
Want to see external device policies in action? Watch the video below to learn how they work and how they can help you control the connection of external devices:
How to create a policy that controls selected external devices
✍️Policies in Safetica are evaluated from the top of the policy list based on this evaluation system.
Creating an external device control policy is very similar to creating data policies. You can set up the Action, set External device types, and set data destinations for them.
To set up policies for controlling external devices in Safetica, follow these steps:
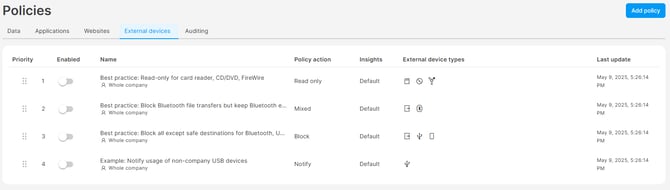
- Go to Policies> External devices and click the Add policy button.
- Enter the name of the policy.
- In the Policy action section, choose what should happen. Actions available for external devices are similar to data policies and you can read more about them here. For external devices, you can choose one more option: Read only – which allows users to open files stored on external devices and transfer files from external devices, but not transfer anything to the devices.
❗There is no read-only action for Bluetooth.
4. The core of each external device policy is selecting External device types, such as USB devices, Windows Portable Devices, Bluetooth devices, etc. Just click the Add device type button to add the external devices you want to control.
✍️Bluetooth device: controls all Bluetooth devices. If you block this external device type, you will basically block all Bluetooth connections (even for keyboards, headsets, mice, etc).
Bluetooth file transfer: controls only Bluetooth devices that contain a storage, so you can transfer files to them. This option does not apply to keyboards, headsets, or mice.
❗Limitation
Only Bluetooth, WPD, and USB mass storage devices are automatically added into Data destinations.
For the others, i.e., card readers, CD/DVDs, and FireWires, Data destinations are not supported.
5. You can also enable Advanced control of individual external device types and set up a different action for each external device.
6. Select users or teams to whom the policy will apply. You can either enter their names directly into the search bar or add them via the user tree by clicking the List of users link.
7. Select how the policy should generate insights. Learn more here.
8. Switch the Policy status to Enabled.
9. Save the policy. The saved policy will be added to the top of the policy list.
10. Drag-and-drop the policy to its correct position within the list.
How to find records of blocked or connected devices
Records of connected and blocked external devices can be found in the External devices section.
To find out which external devices were blocked, use the Actions > Block filter:
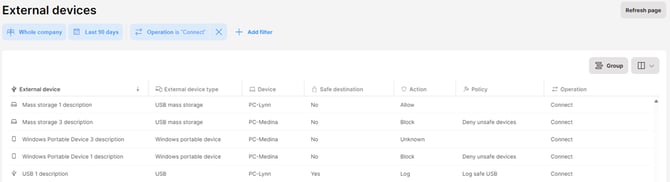
To see which external devices were connected, use the Operations > Connect filter:
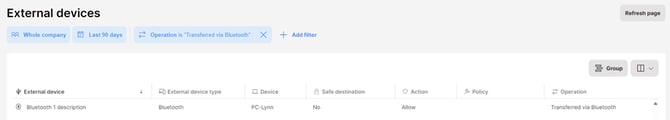
To see to which external devices files were transferred via Bluetooth, use the Operations > Transferred via Bluetooth filter:
Example: Blocking file transfers to USB and Bluetooth devices that are not considered safe by the company
The admin is worried about data leaks, so they decide to block file transfers to USB and Bluetooth devices that are not considered safe by their company:
1. First, the admin adds company devices into Safe destinations in the Data destinations section.
2. Then they create a policy that controls USB and Bluetooth devices as follows:- Check Advanced control of individual external device types.
- USB devices are blocked.
- Bluetooth devices are logged (to allow the connection of devices without storage like mice, keyboards, or headsets, but to see what devices are connected).
- Bluetooth file transfer is blocked.
- The policy is applied to All except safe destinations for all three external device types.
3. Then the admin enables the policy, saves it, and then drag-and-drops it to its correct position within the policy list.
FAQ
Q: Is it possible to control Bluetooth on macOS devices?
A: No, auditing and protecting Bluetooth devices and Bluetooth file transfers is not possible on macOS yet. Also, it is not possible to control card readers, FireWire, and Windows Portable Devices (WPD). On macOS, Safetica only audits and protects USB storage devices.