Data destinations: define your perimeter
Data destinations is a catalog of destinations that can be used to add more granularity to policies.
Introduction
Data destinations is a catalog of destinations that can be used to add more granularity to policies. It complements data classifications and policies and enables admins to treat destinations in their custom and desired way.
In Data destinations, you can manage:
- automatically-detected destinations to which data was transferred by users (such as external devices, printers, websites, network paths, or email domains)
❗From external devices, only Bluetooth, WPD, and USB mass storage are added automatically. Others (i.e., card readers, CD/DVDs, and FireWires) are not supported in Data destinations.
- destinations added manually by admins (for now email domains, websites, and network paths).
You can organize destinations into groups, decide which are Untrusted or Safe, and use them in policies for more granular control.
Data destinations in action
Want to learn more about data destinations? Watch the video below:
How data destination management works
Data destinations management is based on a simple system with 3 columns:
You can add new destinations and groups, move and copy destinations to different groups, or remove destinations and groups. The order of destinations within columns does not represent priority, so you can order them as you want.
✍️Click a group to see its details and perform basic management (e.g., add a new group, rename it, delete it, or move it between the Untrusted and Safe destinations columns; add new destinations into a group, move or copy destinations to another group, or remove destinations from a group).
✍️Click a destination to see its details (e.g. when it was last used and by whom, its ID numbers, etc.). Based on these details, you can decide whether the destination is safe or untrusted.
1. Unassigned destinations
Your “inbox” with destinations that were auto-detected.
By clicking a destination from this list, you can view its specifics and determine which user moved data there.
To save a destination either as Safe or Untrusted and control it via policies, just drag-and-dropping it into the appropriate column.
You can also apply policies specifically to selected destination groups.
✍️Use the Unassigned destinations search bar to find specific destinations.
Destination suggestions
❗Suggestions are only available in cloud-hosted Safetica.
Destination suggestions help admins efficiently manage unassigned data destinations by identifying and highlighling those that are frequently used and need attention. The goal is to prioritize important, frequently used data destinations rather than clearing the entire Unassigned destinations list.
✍️Safetica provides suggestions but never automatically assigns any destinations as Untrusted or Safe. That must always be done by the admin manually.
How destination suggestions work
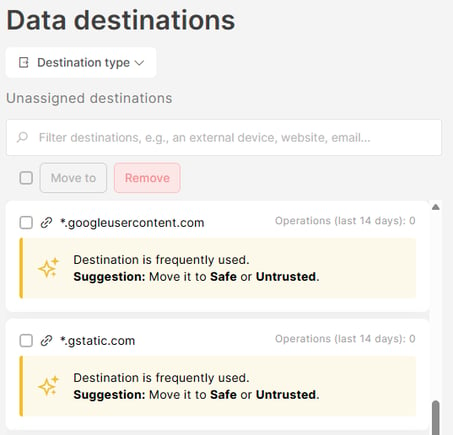
- Suggested destinations appear at the top of the Unassigned list and are highlighted with the message: "Destination is frequently used. Suggestion: Move it to Safe or Untrusted."
- You can assign one or multiple suggested destinations by:
- Drag-and-drop: Simply drag the destination(s) and drop them into the appropriate column or group.
- Bulk move: Select destinations via the checkbox. Click Move to, and select either Untrusted destinations or Safe destinations or a specific group.
2. Untrusted destinations
Destinations that are not part of a secure company perimeter, and you need to control them in a specific way. Items added here can be controlled by granular data policies.
Example: A company blocks uploads of files to all websites. The marketing department, however, needs to upload various media to their online content management system.
When the blog URL (e.g. blog.company.com) is detected and appears under Unassigned destinations, the admin can move it to Untrusted destinations and create a new specific data policy for the Marketing team, for whom upload to blog.company.com is allowed.
3. Safe destinations
Trusted destinations that are part of a secure company perimeter (e.g. company emails or emails of business partners, a file share within company intranet, company USBs, etc.). Items added here can be easily added as exceptions within data policies.
✍️It is best practice to assign company devices and domains into Safe destinations.
Example: A company has an “Block non-company USB drives” policy that allows file transfer to company USBs (since they are considered safe), but blocks transfers to all other USBs.
When a new company USB is used for the first time, it will appear in Unassigned destinations. The admin can then move it to Safe destinations, and the “Block non-company USB drives” policy will start applying to it.
How to filter data destinations
Advanced search: Search for a particular destination across all three columns. Enter details related to it - you can search using any available information about the destination (such as the serial number, vendor ID, hardware ID, or other technical info).
Destination type filter: Filter out data destinations of a specific type, such as all e-mails, external devices, IP addresses, network paths, network printers, printers, and websites.
Example: To view only websites, select Websites in the Destination Type filter. This will display all website destinations in the section.
Read next:
How to manually add new destinations
Destination management: How to move, copy, or remove destinations
Group management: How to add, rename, move, and delete groups


