Data policies: How to create data policies
Protect your data from leaking out of your company. Learn how to set up data policies and configure additional sections, including data classifications, actions, or the option for Shadow Copy.
Introduction
Creating data policies is a bit more advanced than creating policies for applications or websites. They work in a similar manner but have more sections that need to be configured. Before creating a data policy, have a look at setting up policies for applications and websites.
Data policies in action
Want to see data policies in action? Watch the video below to learn how they work and protect your company from data loss in Safetica:
How to create a data policy
✍️Data policies follow the same evaluation system as application, web, and auditing policies.
To create a new data policy, navigate to Policies > Data and Add policy. Data policies have the following extra sections:
✍️A newly created policy is disabled by default. You can enable it:
- in the policy detail by changing the policy status on the right side or
- by toggling the button in the list of policies in the Data tab of the Policies section
1. Data classifications
Here you can specify the data that the policy will target.By default, All data is selected, applying the policy to all files transferred to specified destination types (e.g. to all data sent via email, all data uploaded to the web, all data copied to external devices, etc).
To modify that, click Browse and select one or more data classifications (learn how to create data classifications here). Only files classified with selected data classification(s) will be affected by the policy.
❗Disabled data classifications do not show up in policies.
2. More advanced policy actions
You can choose what policy action should happen when the policy is applied (i.e. the user transfers files to a selected destination):
- Allow: The file operation is allowed.
- Log: The file operation is silently recorded without the user being notified. The policy silently records both allowed operations and operations that violate the policy.
- Notify: The user is shown a notification that the operation violates a policy. There are 2 types of notifications, depending on the destination type:
- Interactive notifications: For web upload, email, instant messaging, and git, the notification allows the user to choose whether to proceed or cancel the operation. If the user decides to proceed, the action is performed and recorded.
- Informational notifications: For print, virtual print, Remote file transfer (RDP), external storage devices (USB, memory cards etc.), network file share (SMB etc.), and cloud drive upload, the notification serves as an informational message only. The user cannot cancel the operation via the notification – the operation is performed and recorded.
- Block: Activities that violate a policy are completely blocked and recorded. Allowed activities are only recorded.
- Block (with override): Certain users are allowed to override a blocking policy, if they provide a reason for performing the file operation. The reasoning is linked to the record about the file operation. If they choose to override the policy, the operation proceeds and is recorded; otherwise, it’s blocked and recorded.
🍏macOS devices: Block (with override) is not supported on macOS.
Learn more about the differences in features between Windows and macOS here.
If you want to learn more about Dynamic action, read this article.
What destinations does this policy apply to?
In the drop-down below, you can also select to which destinations and destination groups from your Data destinations the policy will apply. This allows the policy to be specifically applied to files transferred to chosen destinations:
- All destinations: The policy will apply to all data destinations.
- All except safe destinations: The policy will apply to destinations in the Unassigned and Untrusted columns.
- Only safe destinations
- Only unassigned destinations
- Other...: You can choose specific destination groups to which the policy will apply.
Example: In a company, uploads to all file shares are blocked. The only exception is upload to a file share that is part of the company’s intranet and is considered a safe destination.
✍️By clicking Advanced control of individual destination types, you can configure distinct settings (both action and destination) for each destination type.
3. Destination types
The core of each data policy is selecting destination types, such as Email, Web upload, External storage devices, etc. 
Here you can find more details about individual destination types:
| Destination type | Details |
| 🍏AirDrop |
|
| Cloud drive upload |
|
| Copy to clipboard |
|
|
|
| External storage devices (USB, memory cards, etc.) |
|
| Git |
|
| Instant messaging |
|
| M365 file sharing |
|
| Network file share (SMB etc.) |
|
|
|
| Remote file transfer (RDP) |
|
| Screen capturing |
|
| Virtual print |
|
| Web upload |
|
🍏Learn more about the differences in features between Windows and macOS here.
4. Options
Enable Shadow copy: Enable the Shadow Copy feature so that the policy can start creating shadow copies (copies of files that caused an incident). Learn more about Shadow Copy here.
FAQ
Q: Does Safetica block or audit FTP operations? Can I control FTP file transfer?
A: No, Safetica does not support auditng or blocking FTP file transfers.
Q: Can I create a policy to audit or block git on macOS?
A: No, auditing or blocking git on macOS is not supported yet.
Q: How can I block file uploads to all instant messaging (IM) applications except for a specific one (e.g., WhatsApp), without blocking the running of the apps themselves?
A: To allow uploads for a specific IM application while blocking others, change its category for both applications and websites from Instant messaging and VoIP software to a different category (learn more here). This will prevent data policies targeting Instant messaging from applying to the selected app.
Q: Can Safetica protect against copy and pasting?
A: Yes, it can. Create a data policy for the Copy to clipboard destination type.
A: Yes, it can. Create a data policy for the Screen capturing destination type.
Q: Can Safetica prevent a user from deleting sensitive files or sensitive data?
A: No, Safetica does not audit or block delete operations, since they are not related to data loss.
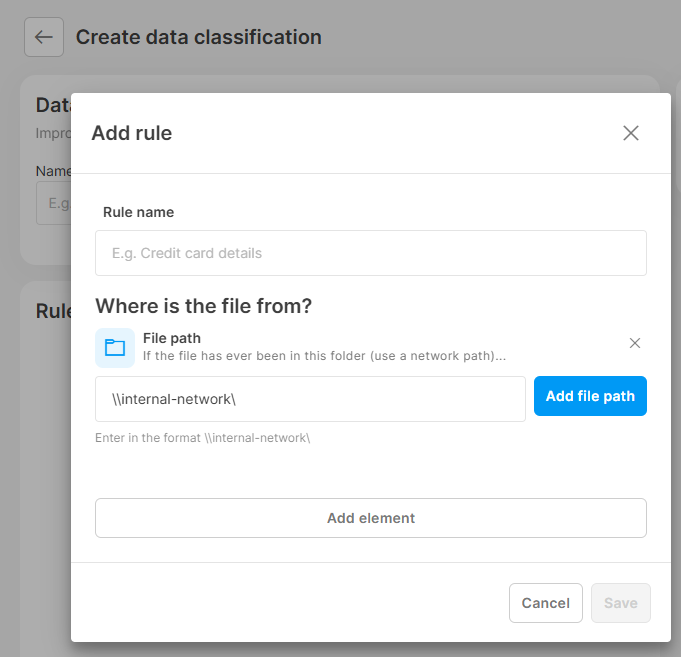
Q: How can I protect files from a specific folder or file path? How can I set up a data protection policy with a specific source file path for specific file transfers?
Read next:
Data classification in Safetica
Policies: How they work in Safetica