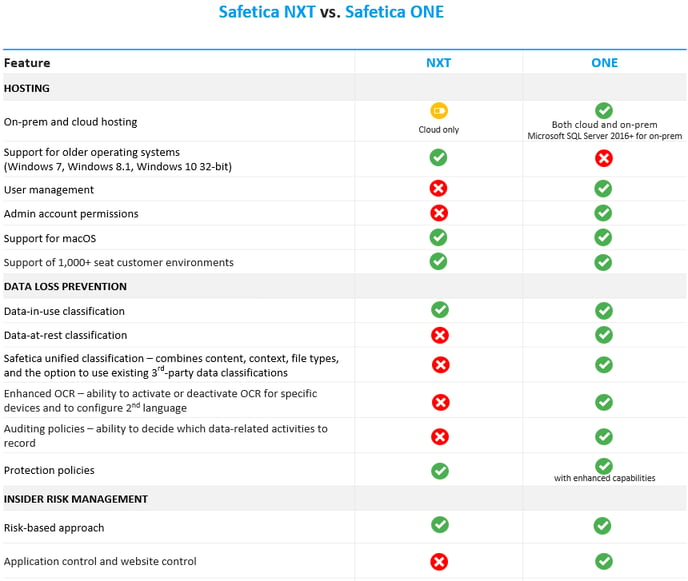
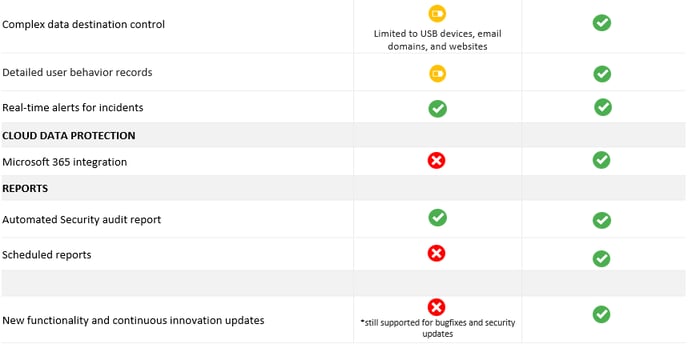
Support of Safetica NXT features in the new Safetica
Learn what features you get after migrating to the new Safetica, which Safetica NXT features have been discontinued, which will be added later, and which require reconfiguration.
Article last updated: March 2024.
In this article, you will find:
Requirements for operating system and Safetica Client
Ensure your system meets the necessary criteria for the new Safetica:
|
New Safetica requires
|
Details
|
|
Safetica Client
|
- Update to version 10.4 or newer
- Older Safetica Clients will stop working after the upgrade to the new Safetica, but you will be able to update them remotely later.
|
|
Operating systems on devices
|
- Supported operating systems: Windows 10 (64-bit), Windows 11 (64-bit), macOS 10.15 and newer.
- Safetica Clients on older systems will temporarily continue working as Safetica 10.4 Clients. You won’t be able to update them, and they will lack support for new features added to Safetica in the future.
|
New features you get in the new Safetica
Discover enhanced capabilities in the new Safetica:
|
Feature
|
What it offers in the new Safetica
|
|
Safetica unified classification
|
- Significantly boosts data classification capabilities. You can classify files based on their content, file type, origin, or third-party classification that you are already using.
- These approaches can be combined to create powerful, very detailed classification rules.
Learn more about data classification in the new Safetica here.
|
|
Application control and web control
|
- Policies to allow or block specific websites or apps.
- Built-in activity categorization to simplify understanding of user activity.
Learn how to set up application and website policies here.
|
|
Admin account permissions
|
- Assign permissions to registered admin accounts.
- Control access to features and user groups.
- Admin accounts are registered similarly to Safetica NXT - you send a registration email to an email address, which is authenticated through Microsoft Azure.
Learn more about how to change permissions here.
|
|
Data discovery
|
Data discovery searches your devices for files with sensitive data that have not been accessed or used for some time.
Learn more about Data discovery here.
You can configure Data discovery based on based on these instructions.
|
|
User management
|
- Assign or remove licenses to and from specific end users for even more control.
Learn more about licensing in the new Safetica here.
Learn how to assign or remove licenses to/from end users here.
|
|
Scheduled reports
|
- More detailed and flexible reports.
- Configure report sets with specific information, how often they will be sent, and their recipients.
Learn more about scheduled reports here.
|
|
Cloud security for Microsoft 365
|
- Integration with Microsoft 365 enables audit and control of email and file operations that occur in the cloud, even via unprotected devices.
|
|
Data destinations
|
- Data destinations are no longer limited to USB devices, email domains, and websites. You can control many destination types, such as:
-
- physical and network printers
- network paths
- removable devices
- email domains
- websites
Learn more about Data destinations in the new Safetica here.
|
|
Auditing policies
|
- Control which data-related actions are recorded and for which users.
Learn more about Policies in the new Safetica here.
Learn more about Auditing policies in the new Safetica here.
|
|
OCR
|
- Activate/deactivate OCR for specific devices.
- Configure a second language.
Learn more about OCR in the new Safetica here.
|
|
Network layer integration
|
- Improved audit and control of network activities, such as sending email via IMAP applications (e.g. Mozilla Thunderbird), thanks to Safetica integration into the system's network layer.
|
Deprecated features not available in the new Safetica
The following features will not be available in the new Safetica:
|
Deprecated features
|
Details
|
|
Automatic assignment of destinations as untrusted or safe based on smart analysis
|
- The new Safetica does not perform smart analysis, so you select safe and untrusted destinations manually.
|
|
User behavior
|
- There is no dedicated User behavior section with assigned risk and its reasoning. You can view user activity in the new Safetica console sections focused on data, app, and website activity.
|
|
Shadow IT
|
- Shadow IT in Safetica NXT allowed you to identify risky activities that happened in your company. This feature is discontinued, but you can find powerful alternatives in the new Safetica including blocking undesirable activities.
To block risky activities in the new Safetica:
You must manually select which app and website categories you want to block:
- Create a new app/website policy.
- Click Add application / Add website.
- Select the Categories tab and select the app/website categories you want to control.
To see risky activities:
- Go to the Apps/Websites section and in the Blocked activity tab, you can see all applications/websites that were blocked by policies and might, therefore, be risky.
- You can also filter a specific app/website category by clicking the Add filter button.
|
If you have concerns about the sunset features, please let us know at support@safetica.com.